Quantum applications
Quantum computers are expected to facilitate major advancements across industry, including in finance, drug discovery and material science, with applications such as:
![]()
Optimising logistical challenges and processes
![]()
Accelerating pattern discovery and machine learning
![]()
Solving complex mathematical problems
Threat to cryptography
Quantum computers also pose a serious risk to today’s encryption systems. Current cryptographic algorithms such as RSA rely on mathematical problems that would take classical computers millions of years to solve. In contrast, a quantum computer could crack the same encryption in days, hours, or even seconds.1 A classical computer is estimated to take around 300 trillion years to break RSA encryption, while a quantum computer could do so in approximately 10 seconds.2
Researchers have already demonstrated quantum techniques capable of breaking RSA keys, albeit small ones, proving that the concept works.3 Shor’s algorithm, developed in 1994, can factor large numbers exponentially faster than classical algorithms, and various national security agencies, including the Australian Signals Directorate (ASD) and the United States’ National Institute of Standards and Technology (NIST), have recognised it as posing a threat to RSA encryption.4
Risk for previously compromised data
As the expected timeline for commercially useful quantum computers continues to shorten, cybersecurity stakeholders, particularly financial institutions, need to ensure they are prepared for the imminent threat of quantum hacking.
The threat to encryption is particularly relevant for financial institutions. RSA algorithms—widely used to secure global payments and transactions—will not withstand quantum decryption.
If these protocols fail, the consequences could be severe: breaches of sensitive data, disruption of critical financial systems and falsified transactions or identities.
This presents a major issue for data with long-term sensitivity, and may significantly change the risk calculus for cyber incidents where encrypted data is involved. While previously, organisations may have taken comfort in the impracticality of decryption, the existence of quantum decryption capabilities may mean this is no longer something that can be relied upon in some high-risk circumstances.
From theoretical risk to practical challenge
Critically, security agencies no longer see the quantum threat as a theoretical risk.
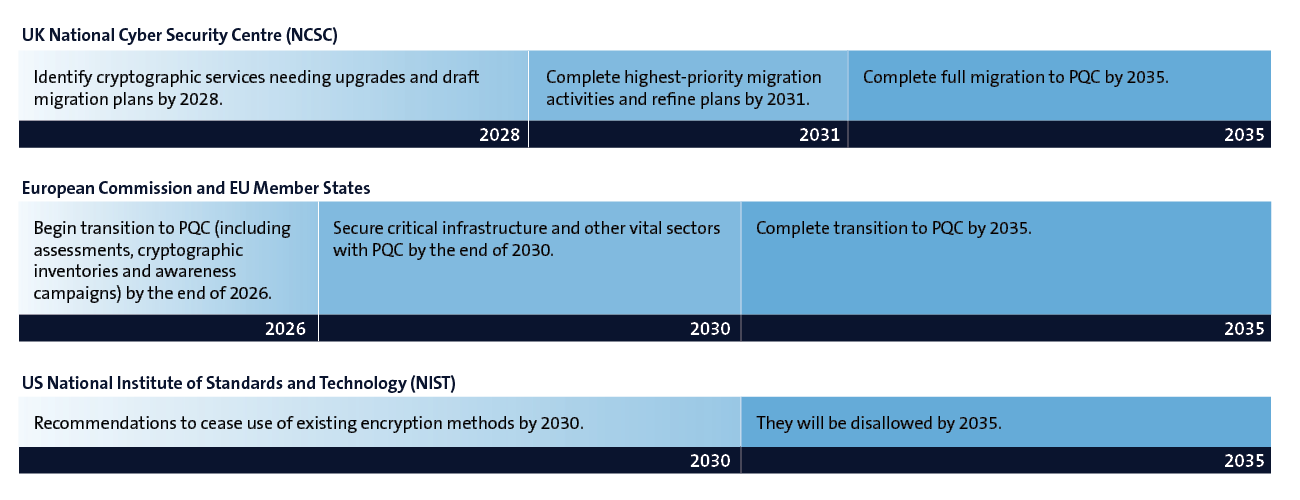
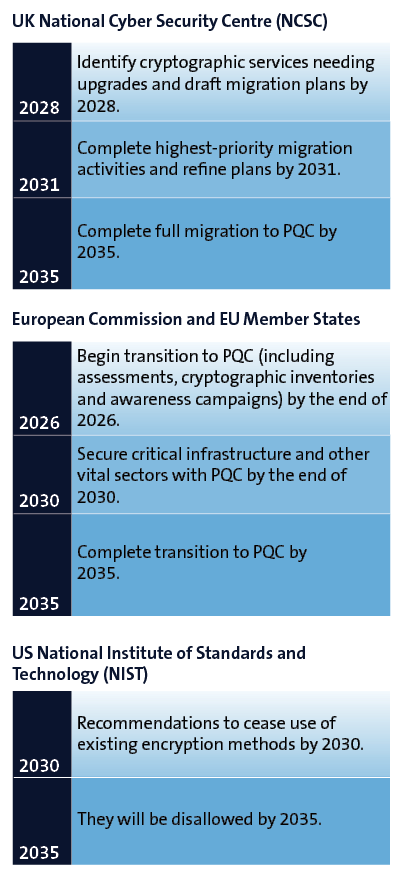
The 2025 ASD Information Security Manual recommends that traditional encryption methods, including 2048-bit RSA, should be phased out by 2030 in favour of 'post-quantum cryptography' (PQC) algorithms.6 These are encryption algorithms that are designed to be resistant to quantum computing decryption.
NIST approved three quantum-resistant encryption algorithms in 2024,9 while the ASD has released guidelines on what quantum-resistant encryption algorithms organisations will need to incorporate to secure their data, including module-lattice-based and hash-based methods.8
Companies with cyber insurance should closely monitor developments in PQC, with emerging quantum risks expected to be a focus of cyber insurance underwriters as quantum computing continues to develop. Already, Google's Risk Protection Program, which streamlines cyber insurance for Google Cloud customers, has expanded in Australia to include coverage for quantum exploit risks.9 Cyber insurers may soon expect policyholders to take appropriate steps to mitigate risks associated with quantum attacks, including implementing approved PQC algorithms as they become available, or risk voiding their policies.
This position is consistent with the position other security agencies in the UK, Europe and the US have taken.
Timeline for phasing out traditional encryption by key agencies

Footnotes
-
See Cyber experts warn of looming 'quantum hacking' threat: quantum computers could reduce the time to hack encrypted data from a million years to a single day, UNSW Sydney, 8 February 2024.
-
See Chinese researchers break RSA encryption with a quantum computer, CSO, 14 October 2024.
-
See Getting Ready for Post-Quantum Cryptography: Explore Challenges Associated with Adoption and Use of Post-Quantum Cryptographic Algorithms, NIST, 28 April 2021.
-
See Michele Bullock: RBA governor warns banks about quantum computing data threat, Australian Financial Review, 24 October 2025.
-
Guidelines for Cryptography, ASD, 18 March 2025.
-
NIST Releases First 3 Finalized Post-Quantum Encryption Standards, NIST, 13 August 2024.
-
Ibid.
-
See Risk Protection Program, Google.







