The challenge
Assessing compromised data following a data breach is often the most complex, costly, time-consuming and stressful part of any incident response. It is also the most overlooked part of incident response planning.
Delays or errors in data assessments and notifications can lead to customer backlash, regulatory scrutiny and unwanted media attention.
No single technology tool can deliver fast, defensible data breach analysis on its own. Effective outcomes require the right mix of technologies, tailored processes and experienced legal oversight.
Key features
![]()
Trusted expertise and judgement
![]()
Purpose-built, multiplatform offering
![]()
Scalable and AI-powered
![]()
Secure
![]()
Custom reporting
Explore our key features
Our team of leading cyber, privacy and data experts brings decades of breach response and regulatory investigation experience. This expertise helps us efficiently narrow the dataset for detailed review, and assess data to inform your notification strategy—quickly, pragmatically and defensibly.
Pairing expert guidance with leading technologies and tailored workflows.
Rather than relying on one tool to do it all, we combine expert guidance with the right mix of technologies and tailored workflows. This ensures the solution fits your specific breach, not the other way round.
Led by Allens’ legal, review and digital specialists, our approach integrates Canopy’s proven compromised‑data workflows with additional tools to tackle specific data challenges*—whether that’s unstructured data, large spreadsheets, images, audio/video files, foreign‑language content or restricted datasets (eg suspicious matter reporting information). Whatever the data type, we adapt quickly and defensibly.
Why eDiscovery platforms aren't the answereDiscovery tools are excellent for litigation review, but compromised data assessment is a different challenge. When the goal is to pinpoint personal information (PI), link it to individuals and generate defensible notification lists, traditional platforms fall short because they:
|
*In addition to Canopy, tools currently include Nuix Workstation, Nuix Discover, Reveal, RelativityOne, Azure AI Foundry and Python.
For faster, more accurate data assessments and notifications.
We've invested in a suite of market leading technologies so you don't have to.
Unlike eDiscovery tools which use traditional data mining methods (eg keywords, regular expressions and pattern matching), we leverage Canopy’s AI‑driven breach assessment engine. This is purpose‑built to rapidly identify personal information and link it to affected individuals, even across complex data types. We combine this with specialised tools to tackle specific data challenges.
All platforms in [Offering] are ISO 27001 certified and aligned with SOC 2 Type 2 requirements. Data is hosted in Australia within dedicated Allens instances, encrypted both at rest and in transit.
Access is tightly controlled through multi‑factor authentication (MFA) and/or single sign‑on (SSO), with strict user‑access protocols. Every action—user activity and document access—is tracked and logged for auditability.
To assist with stakeholder management and support regulatory notifications.
From the earliest stages of assessment, we generate tailored reports outlining review progress and data attributes identified in the dataset that may impact review and notification strategy.
These reports help you keep internal and external stakeholders informed, manage board and insurer expectations, and meet regulatory notification requirements.
How does it work?
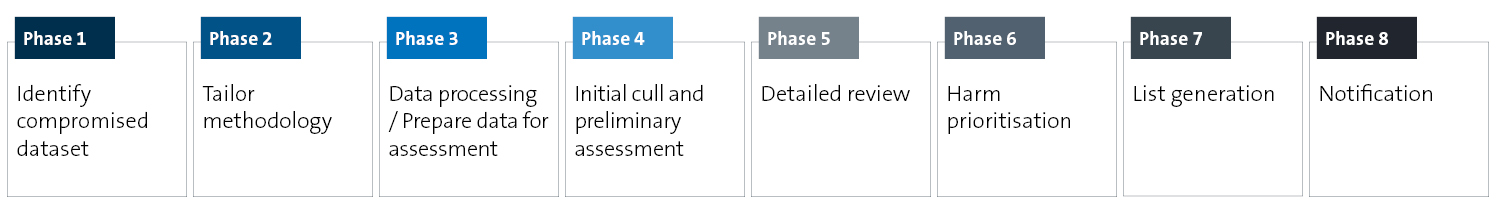

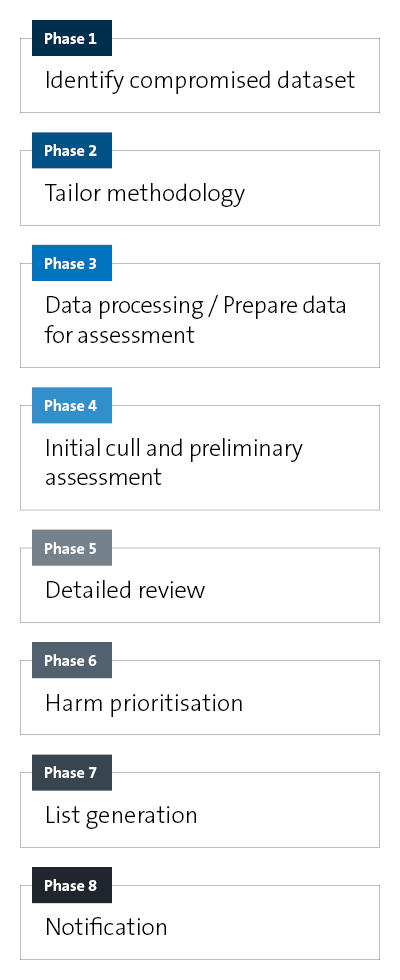
When to use
1. Cyber incidents involving unauthorised access to, or exfiltration of, data. |
3. Accidental data breaches. |
2. Insider threats (eg unauthorised employee access to data). |
4. Personal information access requests. |
Why choose Allens
Trusted expertise and defensibility
Our team of leading cyber, privacy and data specialists brings decades of breach response and regulatory investigation experience. This expertise (combined with our purpose-built, multiplatform offering) helps us efficiently narrow the dataset for detailed review, and assess data to inform your notification strategy—quickly, pragmatically and defensibly. Our proven methodology includes a clear audit trail and decision logs that build confidence with boards and withstand regulatory scrutiny.
Risk, reputational and stakeholder management
We guide you through the entire process, providing visibility and support throughout. We prioritise the highest risk, most sensitive datasets and notifications, helping you mitigate impact and manage relationships with customers, boards, regulators and media.
Cost predictability
Transparent pricing with pre-agreed fixed‑fee components helps you budget effectively, brief insurers, and manage costs while moving quickly.
Expert review capabilities
Our tailored workflows, quality controls and right sized review teams (supervised by Allens lawyers) accelerate the initial assessment, to help refine response strategies while managing time and cost.
Continuous improvement
We refine [Offering] after every incident, drawing on fresh insights and best‑in‑class tools to ensure your response adapts to evolving regulatory expectations and technical capabilities.





