The challenge
Once a cyber incident has been contained, the most crucial part of any response is a company’s ability to rapidly understand the data that has been compromised and the impact on the business, individuals and others.
This phase is also typically the most complex, costly, time-consuming and stressful – it also tends to be the most overlooked part of cyber incident response planning.
It is impractical to conduct compromised data assessments manually at scale, using traditional eDiscovery platforms and solutions. eDiscovery platforms are effective for document review for legal issues but fall short in detailed data assessments, where identifying and analysing personal information (PI) is key. The limitations of eDiscovery platforms include:
- a difficulty in establishing meaningful connections between individuals and their associated PI
- a lack of advanced analytics to identify PI and sensitive data, and
- additional complexity and costs related to generating custom reports and notification lists.
Delays or errors in data assessments and subsequent notifications can quickly attract the ire of affected customers, regulators, industry bodies and the media. They can also have significant regulatory and reputational implications.
Key features
![]()
Holistic overview
![]()
AI-powered
![]()
Scalable and adapted
![]()
Secure
![]()
Custom reporting
Explore below
[insert name] is a multi-platform offering—instead of relying on one tool to do the best it can, [insert name] comprises several leading technologies, custom workflows, proven methodologies, and human expertise to enable manual and technical sensitive data identification, extraction and analysis.
Led by Allens legal, review and digital experts [insert name] delivers a tailored ecosystem of leading tools, platforms and workflows to address the specific needs of the matters. With Canopy's robust and industry leading workflows designed for the assessment of compromised data at its core, [insert name] is complemented by a range of additional tools / platforms to meet the matter's unique data challenges. This multi-platform offering allows us to seamlessly integrate the best of a range to tools to help solve unique data challenges. For example:
- use of specialist AI / ML tools and workflows to assist with the identification and assessment of confidential and sensitive information;
- leveraging GenAI / ML tools for the analysis and tagging of foreign language documents, image, audio, and video files for PI/PHI;
- utilising specialised review teams with multi-platform expertise to identify impacted individuals and associated PI; and
- custom tools and workflows for complex data and reporting needs
Technologies Available: Canopy, Nuix Workstation, Nuix Discover, Reveal, RelativityOne, Azure AI Foundry, Python
Unlike traditional eDiscovery solutions which rely on traditional data mining methods (eg keyword searching, regular expressions (regex) and pattern matching), eDiscovery tools are built around documents and assessment of each document against a legal issues. [insert name] has Canopy's data breach assessment tool at its core to assist with the assessment of compromised data. Canopy is purpose built to speed up PI assessment workflows and is powered by AI to make the assessment of PI and the processes of linking PI to impacted individuals quicker and more accurate.
[insert name] multi-platform approach allows us to use the best tool to solve the unique data challenge. Our wide range of tools allow us to efficiently manage and assess various data types such as unstructured data, large spreadsheets, images, audio / video files, foreign language documents, restricted data such as SMR information and many more. The application of these technologies and scalable review offerings, guided by our legal experts, makes [insert name] an 'end to end' solution for compromised data assessment.
All our platforms are ISO 27001 certified and comply with (or are aligned to) SOC 2 Type2 requirements. The data is securely hosted in Australia within dedicated Allens instances. Data is encrypted at rest and in transit and access to these tools follows strict user access management controls including multi-factor authentication (MFA) and/ or single sign-on (SSO), with all user activity and document access tracked and audit logs maintained.
Our bespoke workflows allow to extract and create customised reports of impacted individuals and associated PI from a very early stage in the assessment of compromised data. These reports can be a very helpful tool for you in managing various internal and external stakeholders for your business, as well as helping you meet your reporting and regulatory obligations.
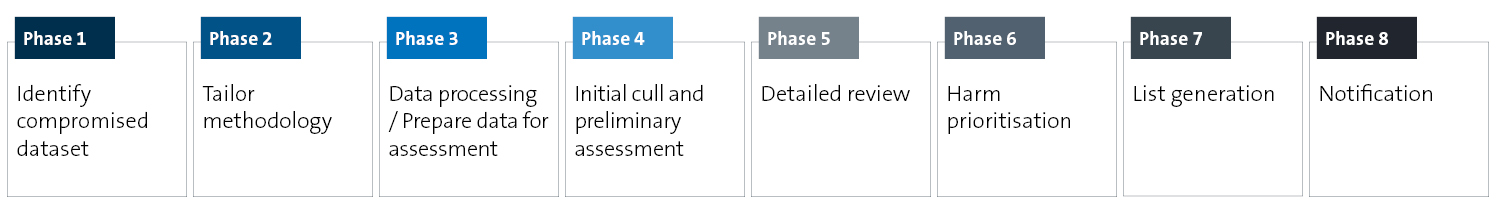
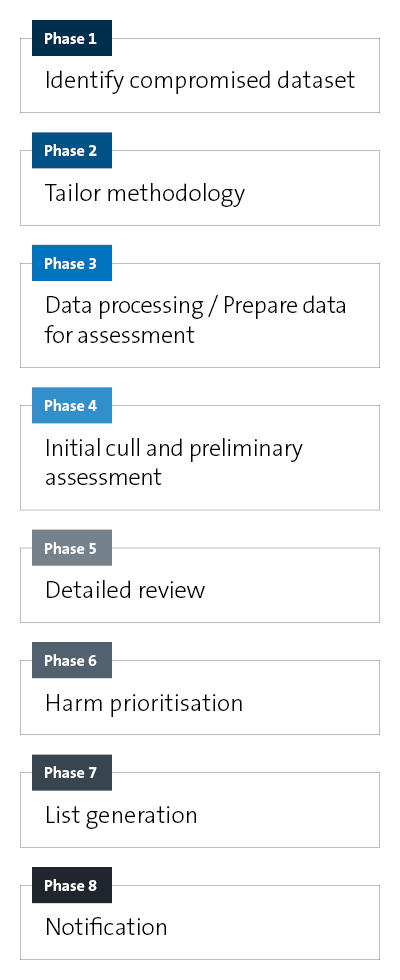
The CIRPIA process

Why choose [insert name of solution / offering?]
Risk, reputational and stakeholder management
[insert solution name] streamlines the data assessment process, helping organisations prioritise higher risk and sensitivity datasets and notifications, and proactively manage internal and external stakeholders and reputational impact.
Trusted expertise
Our team of leading legal and data science experts bring decades of experience advising on data breaches and related regulatory investigations and a comprehensive understanding of how data is structured and stored within organisations. They know how to triage and assess data to inform your notification strategy—quickly, pragmatically and defensibly.
Continuing innovation
We continually [invest in and enhance our solution / refine our approach], incorporating insights from recent incidents and leveraging cutting-edge tools.
Cost predictability
Transparent pricing with fixed fee components helps impacted organisations and insurers predict and manage costs.
Document review expert
Specialising in developing bespoke review workflows to streamline review and utilising lower cost review teams (supervised by Allens lawyers), helping better manage the time and costs associated with the initial assessment of compromised data.
Defensibility
Our robust and proven methodology and traceability of key decisions, gives confidence to boards, regulators and other key stakeholders.
Why eDiscovery platforms aren't the answer
eDiscovery tools are excellent for litigation review, but compromised data assessment is a different challenge. When the goal is to pinpoint personal information (PI), link it to individuals and generate defensible notification lists, traditional platforms fall short because they:
- lack advanced analytics to accurately identify PI and sensitive data across diverse formats
- struggle to connect the dots between individuals and their associated PI—especially in large, unstructured datasets
- add complexity and cost when creating custom reports and notification outputs, slowing down response and inflating budgets.





